This week, I will be discussing the process of incorporating a Managed Network Switch into our network, configuring a mirroring port on the switch, and utilizing Wireshark to capture a password that is being transmitted in plaintext to an HTTP website (not HTTPS). I am conducting this experiment within a lab scenario and retrieving data from my own network. This type of attack simulates a man-in-the-middle attack, which can be executed in various ways, without the user’s awareness. Finally, I will provide some basic measures that can be taken to prevent this type of attack from happening to you.
Equipment & Layout
- Ubiquity USW-Flex-Mini 5 Port Network Switch
- Raspberry Pi 4 – Or any computer that can run WireShark
- Setup & updated
- eth0 connected to our network for remote/admin access
- Additional USB Network Interface for the Raspberry Pi
- eth1 – Will be used to capture traffic
- Target Device
- Another computer that we will capture a password from.
Network Layout:
- Port 1: Network Uplink
- Port 2: Raspberry Pi Admin (eth0)
- Port 3:
- Port 4: Raspberry Pi Monitor (eth1)
- Port 5: Target Device (Laptop)
Adding the Switch to our Network
Add the Network Switch to your UniFi network by plugging it in, and then logging into your UniFi web app. You should see a notice that a new device was detected, select to adopt it into your network. If prompted, you should update your switch as well.
Once your Switch is Adopted, you should see it under UniFi Devices:
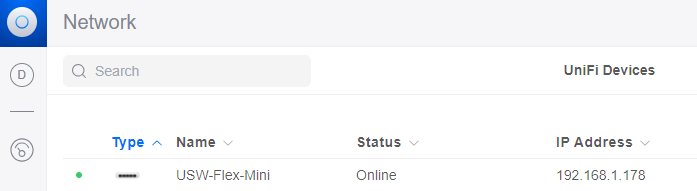
Next, let’s configure a port on the switch for traffic mirroring. A mirroring port duplicates network traffic that is sent to and from the target port. This allows us to spy or listen in on what the target machine is doing on the network, and capture all data sent to and from it.
To do this, first select your switch so the menu pops out on the right. After you have selected your switch, select Ports, and then Port Manager:
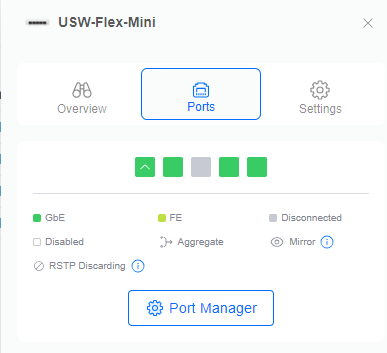
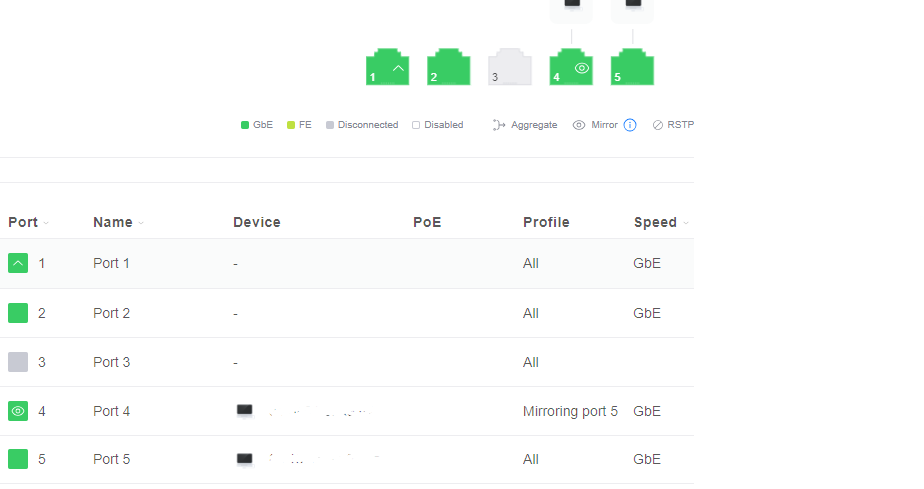
Select the port that we want to enable the mirroring on, Port 4:
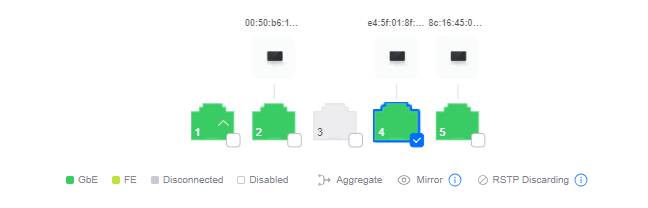
Choose ‘Mirroring’ in the Operation drop-down box, and enter port 5 in the next box as the port to mirror. Finally, choose ‘Apply Changes’ at the bottom.
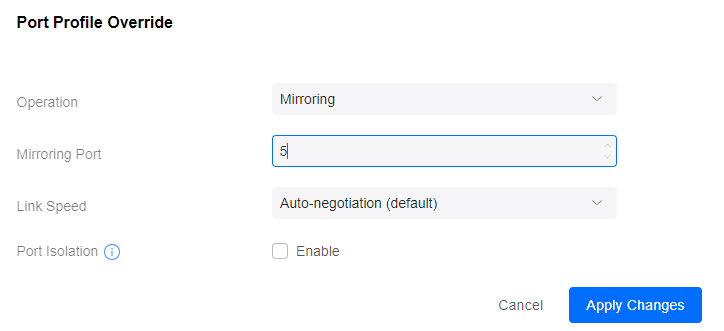
When complete, your ports should look like this:
Install Wireshark
Install Wireshark on the Raspberry Pi by entering ‘sudo apt install wireshark’ and following the prompts.
Select No on this screen:
Using Wireshark
To Start Wireshark from the Terminal, type ‘sudo wireshark’:
Launching Wireshark will prompt you to select an interface to monitor. Since we have eth1 plugged into the mirroring port on the switch, select eth1 by double-clicking on it.
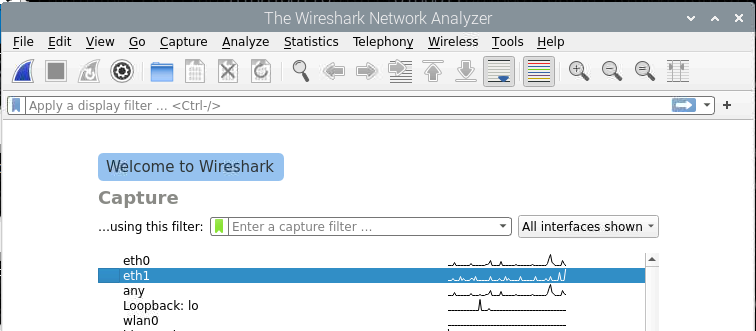
Now that the capture has started, we need to navigate to an (INTENTIONALLY) insecure website. I have set up a page at http://andrewbnortham.com/public/form/index.php that will take a form input, and display it on the page. Once on this website, I entered a Username and Password and hit submit.
After the page loads, return to Wireshark and stop your capture by pressing the stop button at the top. Depending on your network activity, just a few, or thousands of packets have been captured.
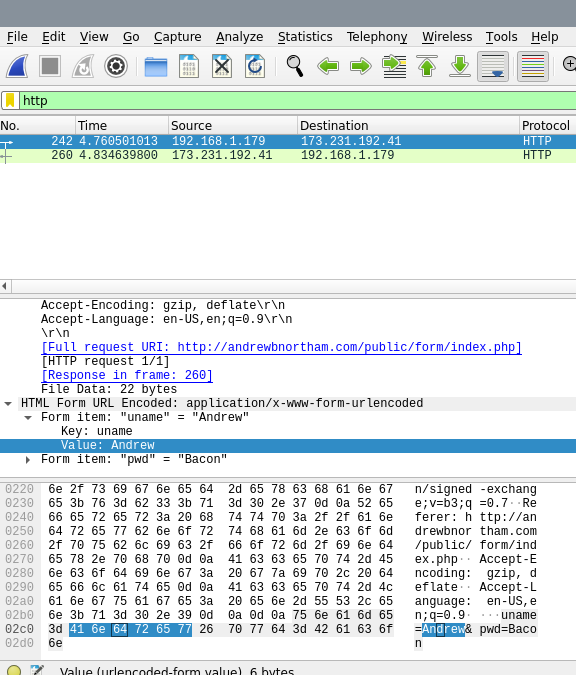
Use the filter box at the top to set a filter, and enter HTTP to show HTTP traffic. Due to the limited traffic on our test network, only 2 HTTP packets were captured. If we click on the first packet, we can see that the form request was transmitted in plain text and the username and password that I submitted were easily captured:
Lessons Learned
It is recommended to implement either WPA3 or WPA2 on your wireless network, as this will encrypt your network traffic and enhance security. Avoid connecting to open or unencrypted wireless networks, as your internet traffic is transmitted in plaintext and can be easily intercepted. It is crucial to never enter sensitive information on a HTTP website and to always check for the padlock icon in your browser, indicating that it is a HTTPS website. The S in HTTPS stands for Secure and ensures that your traffic is encrypted both ways. Physical security is also a critical aspect to consider, so ensure that your network closet is locked and secured from any unauthorized visitors.
